Cross-Site Request Forgery Cheat Sheet

Cross-Site Request Forgery
Cross-Site Request Forgery (CSRF/XSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated. CSRF attacks specifically target state-changing requests, not theft of data, since the attacker has no way to see the response to the forged request. - OWASP
Attack vectors
-
Predictable tokens
Verify if tokens generated by the application aren't easily guessable or possible to be reversed (for example MD5 of iterated integers). -
Lack of Anti-CSRF Token verification
Verify if the Anti-CSRF token value is verified in case of both POST and GET requests.
Verify if the values of Anti-CSRF token like NULL, None, 0, [] could bypass verification.
Verify if the token is required (verification depends on token being present). -
Token used only as a Cookie
Cookie will be attached to the request made from another domain (if there is no SameSite flag). If this value isn't replicated as a header or one of request parameters, it isn't valid defense. -
Token not tied to the user session
Verify if it's possible to use valid token from another session. -
XSS
Having XSS, it is possible to extract CSRF token and use it.
Example:
|
|
-
Brute force
Always check token entropy with at least 1000-10000 probes. If there is some pattern of creating tokens or if they repeat themselves, it is possible to try brute force it. -
Vulnerable subdomain
Having subdomain which is vulnerable to XSS, subdomain takeover or cookie injection, the attacker is able to bypass:
- CSRF-token protection
- Double-submit cookie protection
- Content-type based protection
-
Cookie injection
In case of CRLF-injection of browser bugs, it is possible to bypass double-submit cookie protection through cookie injection. -
Bad PDF
PDF plugin from Adobe support FormCalc scripting - it is possible to exfiltrate Anti-CSRF token. Details here
Additional materials - hints, evasion techniques, other
Using HTTP GET as HTTP POST
This is not CSRF vulnerability, but could make exploitation easier. It allows to exploit CSRF even when SameSite=Lax is used.
Instead of using POST, we are making GET request:
|
|
Into:
|
|
Sending JSON payload as text/plain
Exploitation conditions:
- Server doesn't validate request Content-Type (allows sending text/plain)
- Anti-CSRF or Authorization tokens aren't used
- SameSite cookie is set to None or this situation
|
|
Bypass referer header validation
- Forge URL to include trusted domain:
|
|
- Use META tag within the HTML page that hosts the CSRF attack:
|
|
SameSite loopholes
- SameSite cookie doesn't defaults to Lax in Firefox, IE and Safari (thanks Bug Bounty Reports Explained):
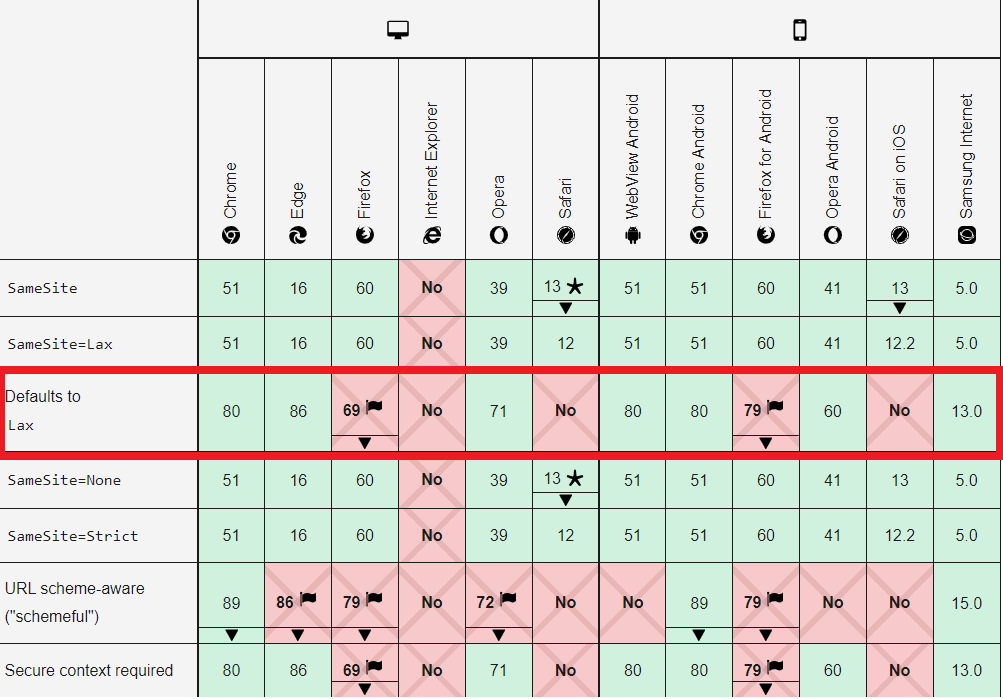
From MDN Web Docs 2021-09-05
- SameSite cookie defaulted (not explicitly set) to Lax by Chrome will be sent in POST requests that occur within 2 minutes of when the cookie was set. SOURCE
Note: Chrome will make an exception for cookies set without a SameSite attribute less than 2 minutes ago. Such cookies will also be sent with non-idempotent (e.g. POST) top-level cross-site requests despite normal SameSite=Lax cookies requiring top-level cross-site requests to have a safe (e.g. GET) HTTP method. Support for this intervention (“Lax + POST”) will be removed in the future.
Magic parameters & headers
|
|
HTML tags - Required user interaction
|
|
HTML tags - No user interaction
|
|
Auto-submitting form
|
|
Silent auto-submitting form
|
|
CSRF Prevention (short version)
More detailed version could be found here - OWASP CSRF Prevention Cheat Sheet
-
Synchronizer Token
Token generated once per user session or for each request. Included as one of the request parameters. -
Double Submit Cookie
Random token which should be included both in a cookie and as a request parameter. -
SameSite Cookie Attribute
SameSite=Strict prevents the cookie from being sent by the browser to the target site in all cross-site browsing context.
SameSite=Lax allows including cookie to the requests, when they are using secure HTTP methods (GET, HEAD, OPTIONS, TRACE) and does top-level navigation.
Implementing SameSite cookies is an additional layer of defense, shouldn't be used as replacement for CSRF tokens.